Zero To Hero - What is Microsoft Defender XDR and Why This Series Exists
Introduction
This blog series is something I’ve wanted to create for some time. Over the years, I’ve worked extensively with Microsoft security solutions and learned a tremendous amount, not just from official documentation, but from community-driven blogs, projects, and shared experiences. These resources have been invaluable in shaping my work. Now, it’s the right time to give something back to the community!
My goal is to sharing practical insights, technical deep dives, and field experience from real-world projects. I want to help others unlock the full potential of Microsoft Defender XDR, because when implemented and optimized correctly, it can transform how organizations detect and respond to modern threats.
This series, Zero to Hero: Microsoft Defender XDR, is designed for security professionals who want more than surface-level information. We’ll go deep in uncovering deployment strategies, configurations, and hands-on scenarios that show what Defender XDR can really do.
My goal is that these articles will enable you to build stronger defenses, respond faster, and ultimately do great things with Microsoft security.
Why this series exists in particular...?
…Cybersecurity is evolving at a pace that challenges even the most experienced professionals. Attackers are becoming more sophisticated, and organizations need tools that go beyond traditional detection and response.
This is where Microsoft Defender XDR comes into play.
What is XDR and why XDR matters in modern security operations ?
But first of all lets take a look what XDR means in general
What does XDR stand for?
XDR stands for Extended Detection and Response. It’s an evolution of traditional EDR (Endpoint Detection and Response), designed to break down silos in security operations. Instead of focusing only on endpoints, XDR extends visibility and response capabilities across multiple sources, meaning endpoints, identities, email, applications, and cloud resources.
Detecting threats faster by leveraging more signals and richer context, disrupt cyberattacks early (preferably automated 😉) and perform even deeper investigations powered by AI-driven analytics.
Why Does XDR matter Today?
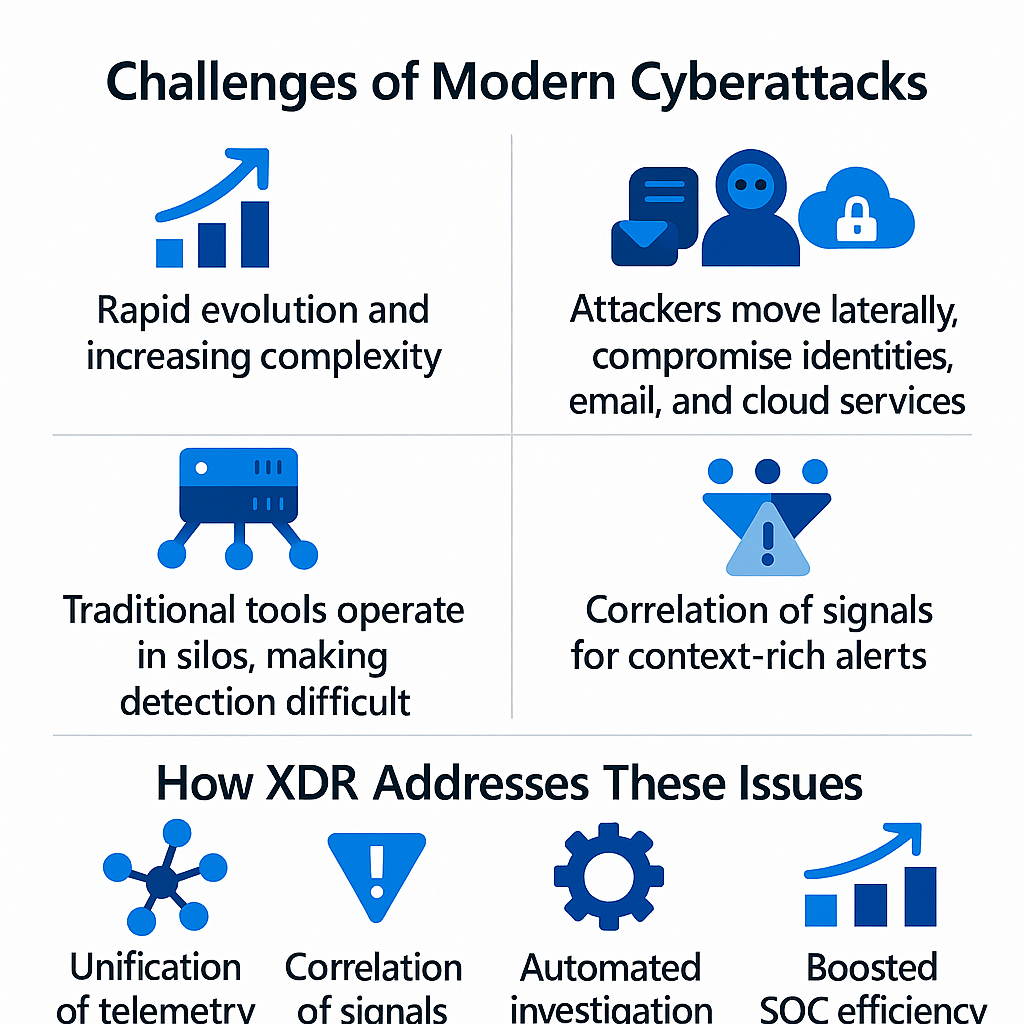
Modern attacks evolve quickly in terms of complexity. Threat actors move laterally, exploit identities, compromise email, and leverage cloud services. Traditional tools often operate in silos, making it hard for security responsible admins to connect the dots quickly enough.
XDR changes that by:
Unifying telemetry from different sources into one platform.
Correlating signals to provide context-rich alerts.
Automating investigation and response to accelerate detection and response times.
Improving SOC efficiency by reducing alert fatigue and enabling faster decision making.
In short, XDR is about visibility, speed, and integration. Three things to stay ahead of modern attackers.
Looking at Defender XDR
Microsoft Defender XDR is Microsoft’s integrated threat detection and response platform,to defend against the full spectrum of modern cyberattacks. Unlike traditional security tools that operate in isolated silos, Defender XDR unifies signals, analytics, and response actions across endpoints, identities, email, applications, and cloud resources. Getting that holistic approach that’s need for enterprise environments.
The Power of Integration: Data Sources in Defender XDR
A core strength of Defender XDR lies in its ability to aggregate and correlate telemetry from a wide range of sources. This data foundation enables to detect complex attack patterns that would otherwise remain hidden in siloed systems.
Data sources
Endpoints:
Defender for Endpoint as a EDR (Endpoint Detection and Response) provides deep visibility into Windows, macOS, Linux, iOS, and Android devices. It collects behavioral signals, process activity, network connections, and threat indicators directly from managed endpoints.Identities:
Defender for Identity integrates with Active Directory and cloud identity providers (like okta), monitoring user authentication, privilege escalation, lateral movement, and suspicious identity behaviors onprem and in the cloud.Email & Collaboration:
Defender for Office 365 protects Exchange Online, SharePoint, OneDrive, and Teams. It analyzes email traffic, attachments, URLs, and collaboration activities to detect phishing, malware, and business email compromise.Cloud Apps & SaaS:
Defender for Cloud Apps (formerly MCAS) monitors sanctioned and unsanctioned SaaS usage, data exfiltration, risky app behaviors, and shadow IT, providing visibility and control over a variety of cloud resources.Other Signals:
With the integration with Microsoft Sentinel, and therefore third-party data sources, or other threat intelligence feeds further enrichment is possible.
How Defender XDR Works: Unified Detection and Response
Defender XDR continuously ingests telemetry data from the sources. Advanced analytics, machine learning, and Microsoft’s global threat intelligence are applied to this data to identify suspicious activities and correlate events into unified incidents.
Incident Correlation:
Defender XDR automatically groups related alerts from different sources (e.g., endpoint, identity, email) into a single incident, providing full attack context and reducing alert fatigue.Automated Investigation & Response:
Built-in automation investigates alerts even further, and can trigger response actions such as isolating endpoints, disabling compromised accounts, or blocking malicious emails, speeding up containment and remediation without admin interaction.Threat Hunting & Deep Investigation:
Security analysts can use advanced hunting tools and queries to proactively search for threats across all data sources, leveraging rich context and historical data to dug even deeper.SOC Efficiency:
By breaking down silos and automating repetitive tasks, Defender XDR enables security responsibles to focus on high-value investigations and strategic defense.
What to expect for the future
This kickoff article set the stage for our journey into the world of Microsoft Defender XDR. We’ve explored what XDR is, why it matters, and how Microsoft’s integrated approach is changing the game for modern security operations. But this is just the beginning.
In the upcoming articles, we’ll move from high-level concepts to hands-on technical guidance. You can look forward to deep dives into Defender for Endpoint, covering real-world deployment, configuration best practices, and advanced capabilities. I’ll break down complex topics, share practical tips from the field, and provide step-by-step guidance to help you get the most out of your security investments.
Whether you’re new to Microsoft security or looking to sharpen your expertise, this series is designed to empower you with actionable knowledge and insights. So stay tuned, get ready to level up your skills, and join me as we go from Zero to Hero with Microsoft Defender XDR!
Sources & Further Information
Microsoft:
Microsoft Defender for Endpoint documentation - Microsoft Defender for Endpoint | Microsoft Learn
Microsoft Defender XDR documentation - Microsoft Defender XDR | Microsoft Learn
Community:
I can highly recommend the following community projects and blogs if you want to learn more about Defender & Microsoft Security
Ru Campbell MVP - Microsoft Security, Identity, Compliance, and Management